How to Force Google Safe Search on DD-WRT

Try Oone of These Two Methods to Force Google Safe Search
These two methods will enforce Google’s safesearch on all computers on your network (keep in mind that this won’t work for cell phones or other devices using cellular data). This is specific to any router using the DDWRT firmware. DDWRT is an open source firmware that is available to be flashed on a number of routers (check the DDWRT website for a list of compatible routers and installation details)
Method #1 of Forcing Google’s Safe Search – Rewrite DDWRT’s Hosts File on Startup
The simplest way to do this is to have your router edit your hosts file on each startup as follows:
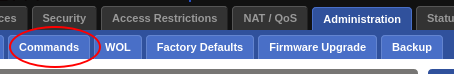
- Go to Administration->Commands
- Click “Edit” and add the following script:
1234echo '216.239.38.120 www.google.com216.239.38.120 encrypted.google.com216.239.38.120 google.com' >> /etc/hostsrestart_dns
- Click “Run Commands”
- Click “Save Startup”
- Done!
What does this do ? It redirects those urls to the ip address of forcesafesearch.com. Your hosts file will be wiped out on every reboot of the router but the script will restore the settings.
While this is a very easy way of forcing safesearch, the disadvantage is that Google could change the ip address of safesearch. In addition, this method doesn’t permit wild cards.
Method #2 of Forcing Google SafeSearch- Use DNSMasq
This method permits wildcards:
- Make sure that you have DNS masq enabled.
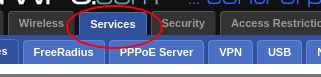
- Services->Additional DNSMasq option Box.
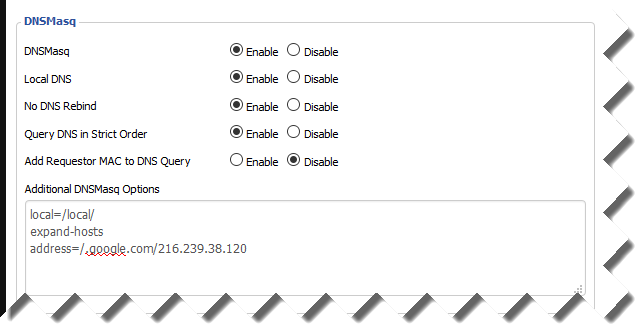
- Insert the following (Note the DOT before google.com, the dot acts as a wild card to pickup any subdomains):
123local=/local/expand-hostsaddress=/.google.com/216.239.38.120
- It should look like this:
- Click “Save” (button bottom of page)
- Click “Apply Settings”
- Done! If it doesn’t work right away you may need to reboot the router (use the button on the Services tab)